Updating the Cert
We at times need to update the NAS cert for the registry. We can see its usage in our Github Runner image build here:
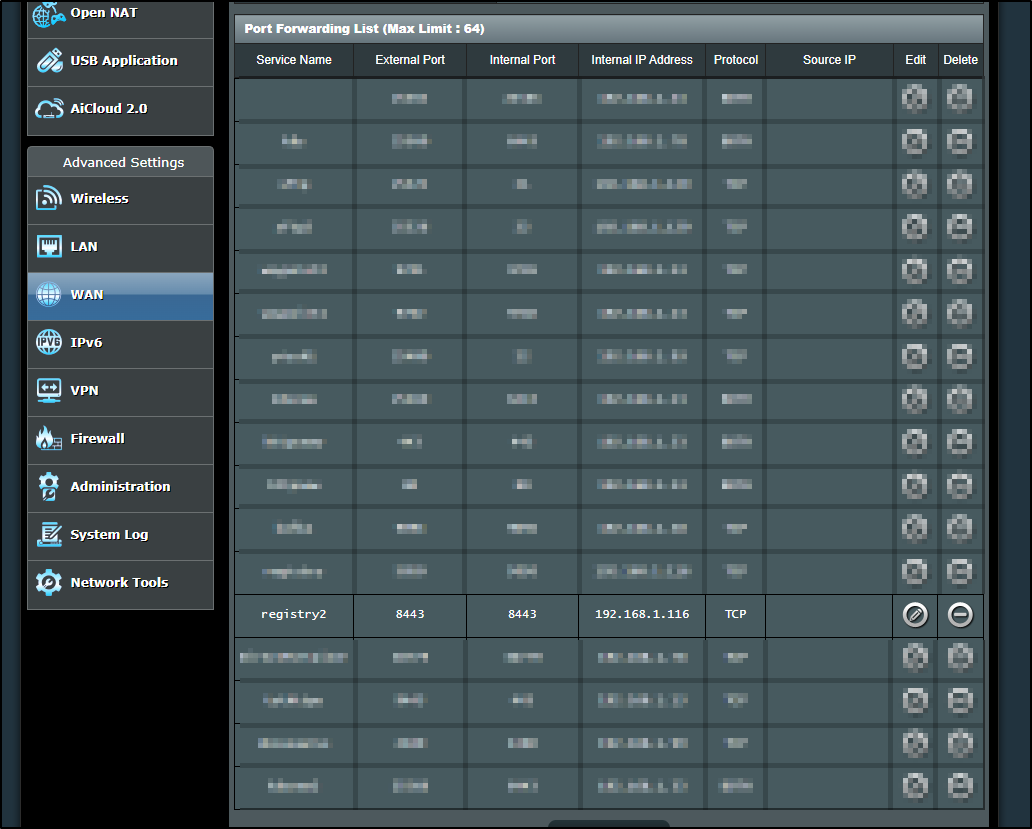
the endpoint "registry.freshbrewed.science:8443" is one of the few NOT serviced by Kubernetes. We can verify that by going to the Firewall and checking the rules on 8443
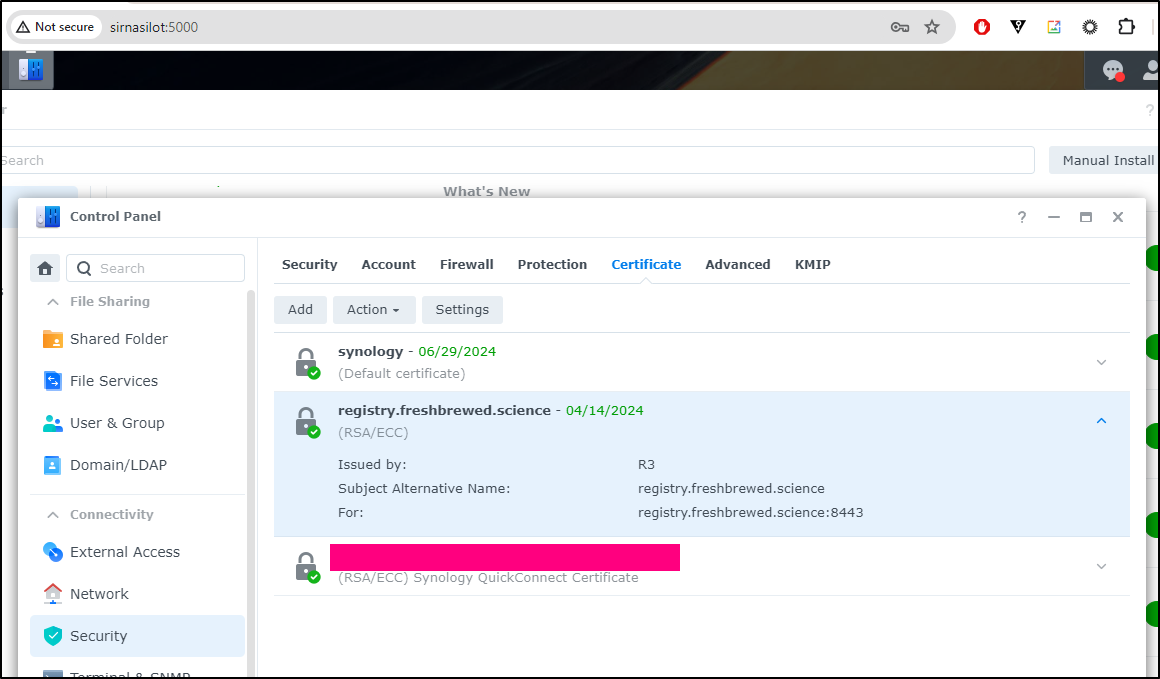
We can double check this by going to the NAS at that IP and seeing the certificate listed in the control panel under Security
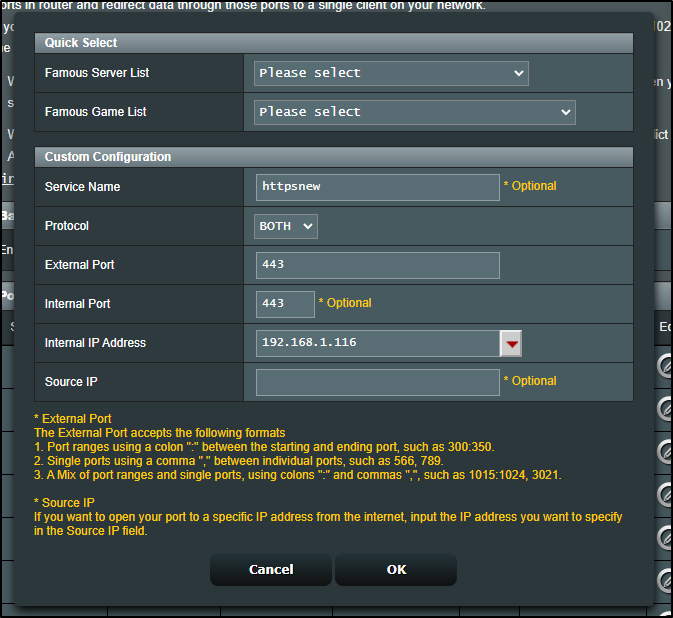
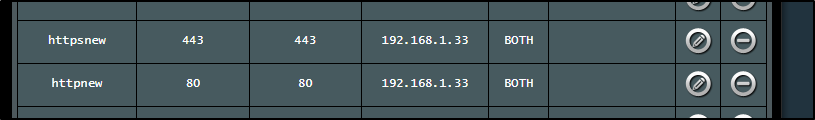
I'll briefly change rules for 80 and 443 from the Int Primary (now 33) to the NAS
Then in the NAS, use Action/Renew certificate
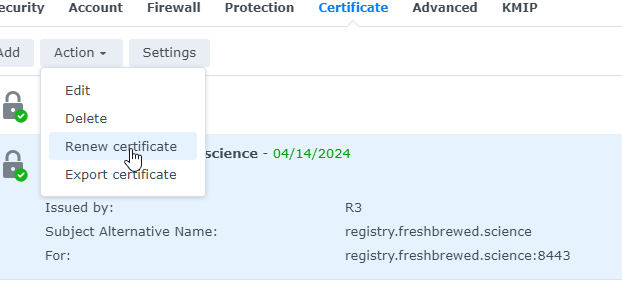
Note to self; consider what happens when you redirect the 443 while using CodeX hosted in K8s - yeah, gonna lose my connection. better save first next time :)
When done, I'll see a new date on all the certs
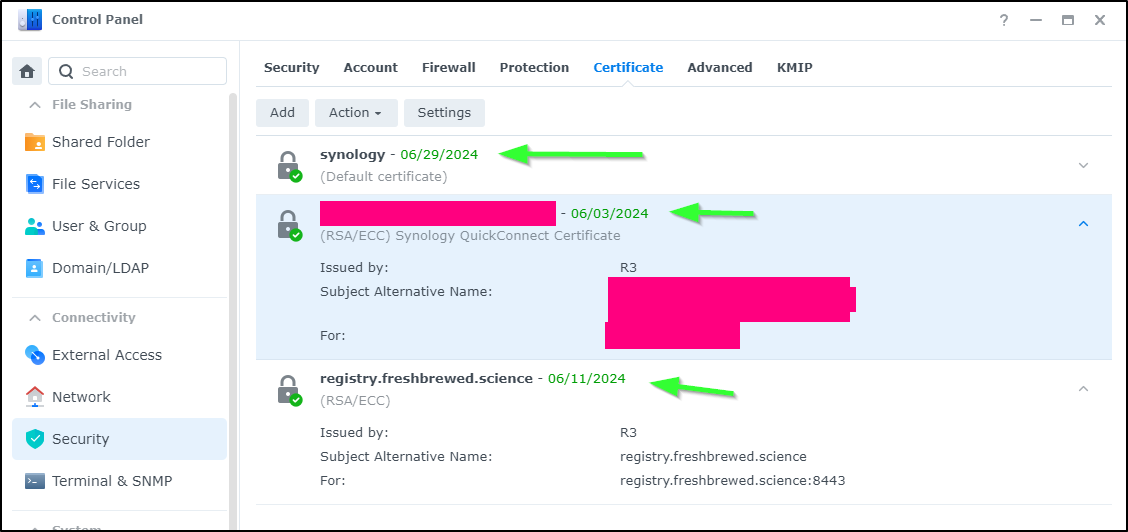
I can then change my my WAN forwarding rules back to K8s
Lastly, let's move our calendar step forward to remember to do this again in the future